Web Application Penetration Testing

What is Web Application Penetration Testing
Testing a web application for vulnerabilities, flaws, and potential security threats include assessing and analyzing the application. Achieving protection for the application against dangers such as hostile assaults, unauthorized access, and data breaches is the aim. Code reviews, penetration tests, and vulnerability scanning are just a few of the methods that are usually used in this process. Organizations may protect confidential information, uphold user confidence, and adhere to industry standards by detecting and resolving security risks.
Web Application Penetration Testing is crucial because it:
- Identifies vulnerabilities before attackers can exploit them.
- Protects sensitive data from unauthorized access.
- Maintains user trust by preventing security breaches.
- Ensures compliance with regulatory requirements, reducing legal and financial risks.
Our Approach for Securing Web Applications
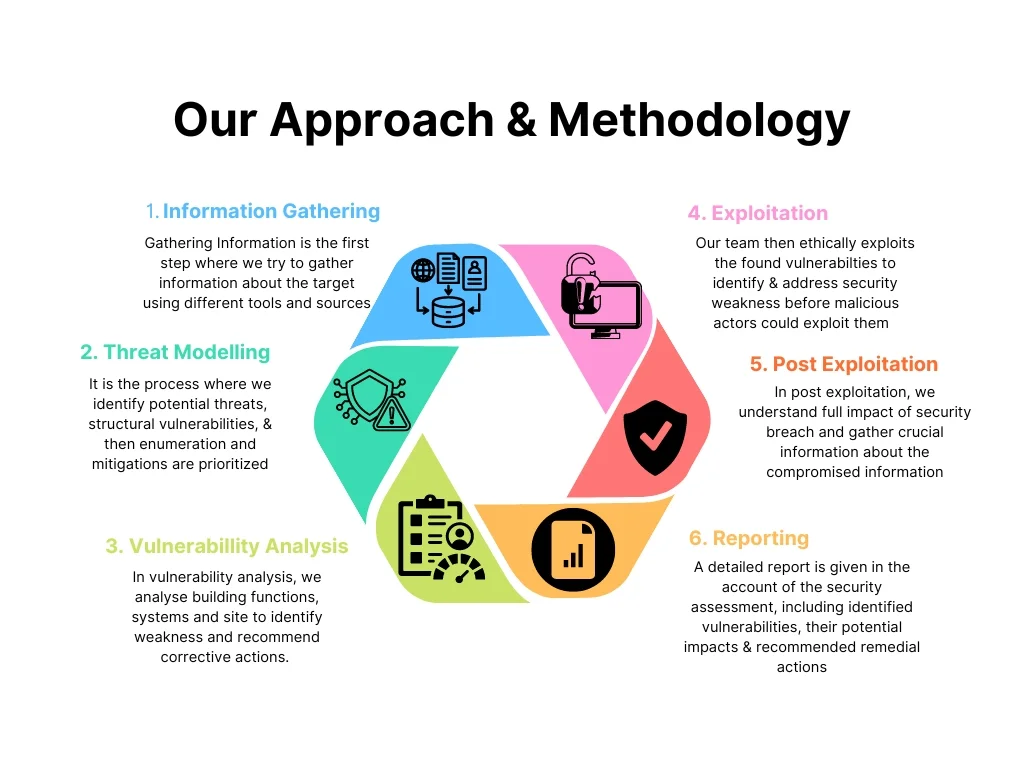
1. Information Gathering: Gathering information is the first step where we try to gather information about the target using different tools and sources.
2. Threat Modelling: It is process where we identify potential threats, structural vulnerabilities, & then enumeration and mitigations are prioritized.
3. Vulnerability Analysis: In vulnerability analysis, we analyze building functions, systems and site to identify weakness and recommend corrective actions.
4. Exploitation: Our team then ethically exploits the found vulnerabilities identify & address security weakness before malicious actors could exploit them.
5. Post Exploitation: In post exploitation, we understand full impact of security breach and gather crucial information about the compromised information.
6. Reporting: A detailed report is given in the account of the security assessment, including identified vulnerabilities, their potential impacts & recommend remedial actions.
Our Deliverables
- Executive Summary: An overarching presentation providing insights into the engagement, highlighting identified vulnerabilities, and presenting recommendations for comprehensive threat mitigation
- Technical Security Report: A detailed, technically-focused document that included proof-of-concept examples and comprehensive exploitation instructions for all identified threats.
- Security Dashboard: A user-friendly dashboard is provided to assist our clients in tracking vulnerability remediation progress, action items, and other relevant information.
Benefits & Impacts
- Risk Reduction: Security vulnerabilities were identified, and solutions with proven methods for enhanced security will be recommended.
- Cost Efficiency: We'll suggest cost-effective risk mitigation measures aligned with our client's business objectives to ensure security without compromising on customer services.
- Customer Trust: The assessment will be conducted with minimal disruption to customer-facing systems, allowing for the identification of vulnerabilities, potential risks, and their impacts.

